m360Encrypt – an Encryption program like no other.
Download m360Encrypt at the bottom of this post. Please read Important Notes first!
I wanted to do a deep dive into encryption, and found there was a lack of transparency and personal control in this sector, as well as a lack of what I consider to be some very essential features. So I set out to make my own encryption program with these goals:
- I want to give users the ability to pass encrypted messages entirely on Social Media (or similarly wide open channels) in a completely save way.
- I want to be able to write record and save my own personal research, thoughts, and writings and know they are 100% safe from prying eyes – even if someone gets a hold of my device.
- I want users to have everything they need contained right inside the program – no installing 3rd party libraries. No complicated command line key generation. No linux shell inside of Windows – just a plain, simple program that does what it says in the easiest way possible.
This was a labor of love. Let me walk you through it.
m360Encrypt uses two types of Encryption:
RSA, which is an asymmetric encryption, can use public and private key pairs instead of a shared password, but only encrypts short messages, and AES 256, which is a symmetric encryption but requires a shared password. The way most encryption algorithms work, including PGP, is by using a combination of the two.
RSA allows you to exchange short messages in a public channel, protected by your key pairs, so it’s perfect for exchanging a password you can agree to share later. AES allows you to then use that password to share longer messages.
Only one person needs to generate a keypair. Let’s call them Bob. And as is tradition – Bob will be exchanging encrypted messages with Alice. Once Bob has generated his keys, he shares his public key with Alice, and loads his private key in the program.
Bob can put his public key anywhere Alice can see it – it doesn’t matter who else sees it. He can email it, post it on his blog, put it on facebook, etc.
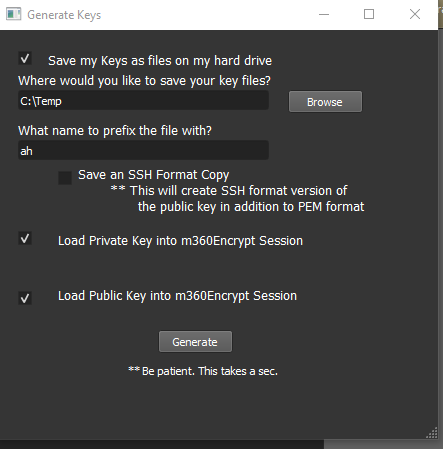
Alice is also running a copy of m360Encrypt. She copies Bob’s public key and pastes it into the bottom window.
Alice is the person choosing the password, encrypting it, and sending it to Bob. She is the Sender, so on the next screen, she uses the “Sender” window to select and encrypt a password. Because she’s the sender, it will encrypt the password with Bob’s public key.
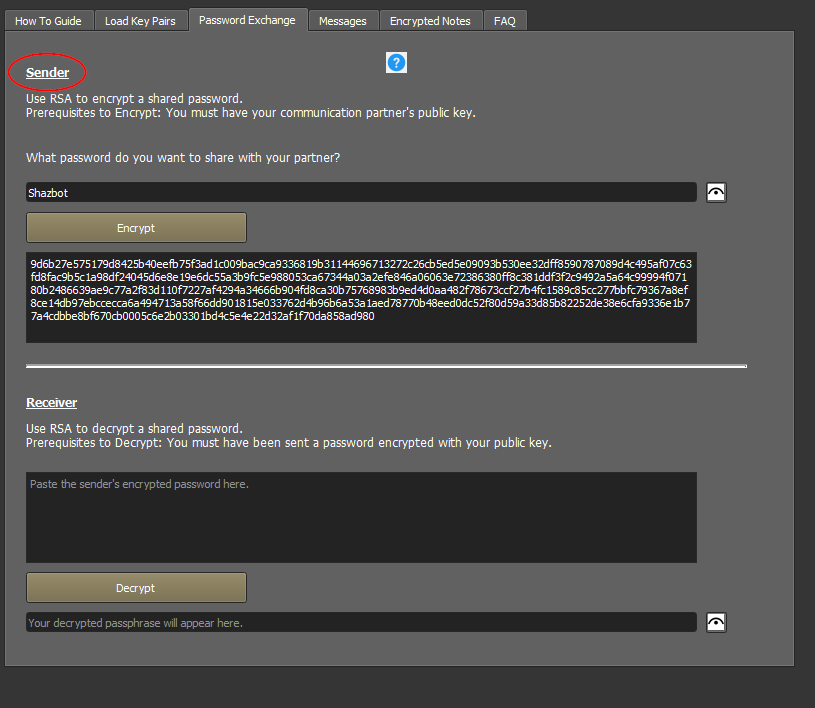
Now she can copy the encrypted password and paste it anywhere Bob can see it
(Email, blog, facebook, etc). Bob will be the only person in the world able to decrypt this password.
Bob copies the encrypted password, and decrypts it.
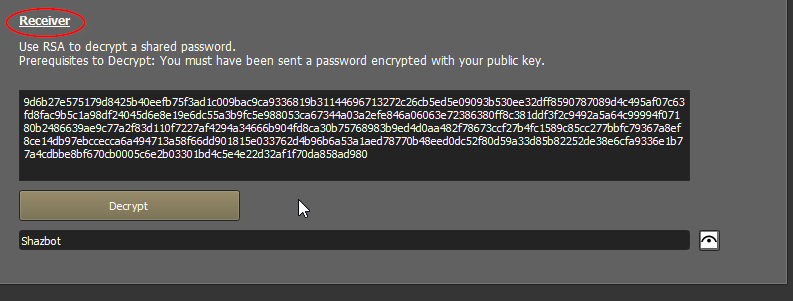
Now they have a password no one else knows that they can use to pass longer AES encrypted messages. So they can use the “Messages” screen.
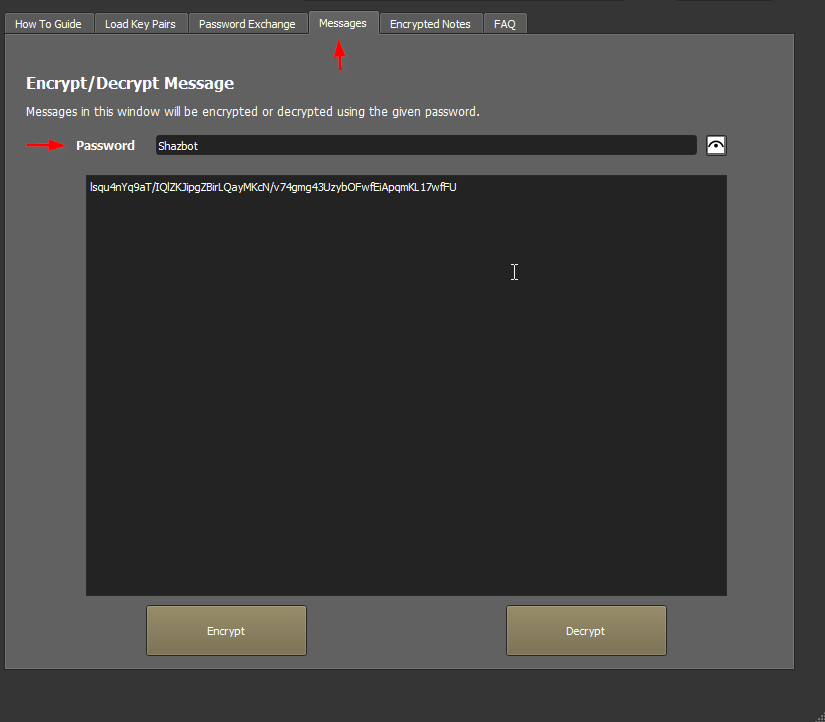
They can post their messages anywhere, and no one will be able to read them except the people who have the passwords.
The final section, “Encrypted Notes” lets users type out text notes, and encrypt them before saving them to their hard drive, or load encrypted note files and decrypt them only in RAM. This will come in very handy for Alice and Bob who might want to remember details of their encrypted conversation.
Important Notes:
Please don’t use this program to do evil things. I made this because I care about privacy, and because I think consumers need to push back against an ever-tightening net of corporate surveillance. I did not make this to help anyone break the law.
It is not signed, so Windows will give you a warning that it cannot verify that it is safe. But it is. In some instances, it even says that it contains a virus. It does not. It contains safe, widely used Python cryptography libraries that, for some reason, Windows doesn’t like sometimes. It will show you a scary red box, just click “More Info” and then “Run Anyway”